Jun
16
Fading Personal Data
June 16, 2010 | 1 Comment
Have you ever looked at your address book and seen an entry for someone you haven’t talked to in years? I usually think to myself “I wonder if that phone number is still good.” Sometimes I even wonder if people are still alive.
A Dutch information security researcher wants to use a concept similar to that to try to protect all that information about us that’s stored on line, according to an article at the BBC. The idea would be to have your information “degrade” over time, just like your confidence in whether that email address for Joanne is still any good.
At initial use to secure a transaction or get useful information from a search all relevant details might be stored. Subsequently details would slowly be swapped for more general information.
It’s an interesting concept. I’ve always been intrigued by the idea of looking to the physical world for solutions to problems in the digital one. I’ve frequently thought it would be interesting to look into mimicking the animal immune system for a computer anti-virus system, for instance.
Of course, Europe has better controls, and a different view, of information security than the US. It’s likely that any system like the one outlined by Dr. Heerde could be mandated here, because unlike Europe, in the US businesses own the information they collect about you, rather than you owning your own information. Still, it’s an idea to feed to the grist mill, and perhaps something interesting will come out the other side.
Apr
22
How to spot an ATM skimming device
April 22, 2009 | Leave a Comment
For those who aren’t aware, there are folks out there who are stealing your ATM information not by breaking into the transaction processing company, but by stealing it from you at the ATM. This process is called “skimming,” and it involves installing a card reader and a camera on the ATM. The card reader gets the information on the magnetic stripe on the back of your card, and the camera watches what you enter for a PIN. I knew these were out there, but it was a surprise to me to see how advanced they were, transmitting information wirelessly to the thieves.
It’s a good idea to try to keep an eye out for these devices, but you have to know what to look for, so I was interested to see a guide on spotting a skimmer. It’s a brief PDF that’s worth the read.
[ Consumerist via Lifehacker ]
Feb
17
Update: First Arrests in Heartland Case
February 17, 2009 | Leave a Comment
It seems that if you steal enough credit cards, then you might actually get arrested. Last week I posted about the Heartland Payment Systems case, and today, Computerworld is reporting that the first arrests have happened in the case. This to me is remarkably swift justice.
The Leon County, Florida Sheriff’s office earlier this week announced the arrests of three area residents — Tony Acreus, Jeremy Frazier and Timothy Johns — for allegedly using stolen credit card numbers associated with the breach.
I was just reviewing some of the Payment Card Industry Data Security Standard information today, and was struck by the requirement to encrypt data when it was in transit. According to all the information I’ve seen so far, this breach happened because someone managed to get a network sniffer in place, and capture transaction data. I may be missing the point, but how were they able to read the traffic if it was encrypted? Did they have the keys, or was Heartland playing fast and loose with the DSS? I don’t understand enough about either the facts in the case, or the DSS to say if this is reasonable or not, but it sure seems like someone at Heartland could be in a world of trouble.
Feb
3
The New Computer Hacking Game
February 3, 2009 | 1 Comment
Perhaps I’m just getting to be an old timer. When I started managing computer systems for the telephone company in the late 1980s, the game was to break into systems primarily to learn something. Occasionally there were malicious attempts to access information, such as the phreak’s setting themselves up with free phone service, but for the most part, the damage to society at large was fairly limited.
Late in January, we learned about a security breach at Heartland Payment Systems. According to coverage at Computerworld, it seems the attackers placed some sort of malware into the Heartland network, and were able to capture an undisclosed number of credit card transactions, primarily from smaller businesses such as gas stations and convenience stores. Heartland isn’t saying how many accounts were compromised, but they process about 100,000,000 transactions per month, and they were apparently notified by the card companies of a possible problem last October, and well you do the math.
People breaking into computer systems these days aren’t doing it for fun, or to learn how things work, or at least they’re not the only ones breaking in. The naive period of hacking adolescence has passed. We’re not looking around in empty houses under construction, we’re breaking into occupied houses and robbing them while the owners are there.
Computer security is serious business, and business has given it very little attention. To make matters worse, the public really doesn’t seem to care either. TJX has a massive security breach: what happens to the stock? It goes up.
Until consumers start caring about how much money lax security is costing them, there will be no change. Since consumers aren’t showing any inclinations to care, the only hope for us is making a criminal negligence complaint against businesses that take absolutely no care of our identities.
Sep
5
Research FaceBook App Recruits for Botnet
September 5, 2008 | Leave a Comment
I’ve blogged in the past about botnets, and it should be pretty clear that they can be powerful entities for good or evil. With human nature being what it is, they’re mostly used for evil. As a botnet controller, I imagine it must be very seductive to look at a popular service such as Facebook and drool at the prospect of all those computers we could recruit. But how to infect them?
Researchers in Greece apparently thought the same thing as well, and they’ve produced a research application called Picture of the Day. This little app claims to display a different picture from National Geographic on your page, and it does that. Unfortunately, it also serves up software to turn your computer into a botnet zombie.
It didn’t take much to get people to install it, apparently. According to the report on Dark Reading:
Interestingly, the researchers did not invite users via Facebook to download the application, but still managed to attract around 1,000 users who downloaded Facebot within the first few days it went live. They merely announced its availability to members of their research group and asked them to pass it to their colleagues. From there it apparently spread to other Facebook users.
As a security-type person, this sort of thing really concerns me. I know that the average user isn’t really all that concerned about security until it bites them in the hinder. I can’t even get developers to be concerned about it most of the time! The spread of social networking sites creates a target-rich environment for the spread of just these sorts of compromises, and it’s not at all clear how to fix it.
May
12
The Anatomy of a Botnet
May 12, 2008 | 2 Comments
There’s been a lot of news lately about botnets. But what exactly is one?
A botnet is a collection of computers that are under remote control. These compromised computers are typically called “zombies.” Zombie computers connect to a command-and-control system created by the owner of the botnet, and listen for commands. These commands can direct them to scan the zombie computer for personal information (such as bank account numbers, credit card numbers and passwords), search for other computers that have known security vulnerabilities that haven’t been patched and infect them as well, or to perform pretty much any action the botnet creator wants. In fact, many botnets have the ability to update the botnet software itself at the direction of the controller, adding new functions as needed. The largest botnets can have hundreds of thousands or even millions of computers under the control of a single individual or group.
Botnets have been used to extort money from internet gambling sites, by establishing so many connections from computers scattered across the internet that real, legitimate users can’t get through. Experts estimate that about 80% of the unsolicited commercial email, or spam, that you receive in your email box comes from 6 botnets.
But how does a computer become a zombie?
It can happen in a number of ways. As I already mentioned, if you don’t keep your computer up to date with patches, another zombie can find your computer and infect it. Another way your computer can become a zombie is if you visit a web site that installs software on your computer without your knowledge. Don’t think that only pornography or “warez” sites are dangerous: malicious software has been discovered on prominent companies web sites as well, as a result of a hacker compromising their security.
Programs such as Yahoo messenger and AOL instant messenger can also be used to compromise your computer. In fact any flaw in a program could potentially infect your computer causing it to become a zombie.
Wouldn’t you notice if your computer was doing things without you telling it to? Not at all. Botnet zombie programs are carefully designed to avoid detection, and anti-virus and anti-spyware programs are typically only as good as their signature creators can make them. They come with no user interface, so it’s likely you wouldn’t notice them.
So what can you do? You should always run your computers behind a firewall, particularly if you’re a home user. Internet sites are available to help you determine how secure your firewall makes you, but don’t rely on just one: try as many as you can find.
The same applies to anti-virus and anti-spyware programs: don’t rely on just one. If you suspect that your computer has been compromised, such as unexplained crashes and strange files, get your hands on three or four of these programs and run them in turn. That way you stand a better chance of finding and fixing the problem.
What are the authorities doing about botnets? Unfortunately, usually precious little. Internet crime is hard to investigate, and since it’s frequently trans-national, even harder to prosecute. There have been some successes.
Ironically enough, sometimes the botnet owner’s worst enemy is another botnet owner. Since these networks can download new programs, it’s possible for one botnet owner to steal another’s network by compromising his or her command-and-control servers, and directing the network to download different software, adding the new network to their existing one.
There has been some research in the last couple of years working on understanding, detecting and fighting botnets, but as of now, the fight is long from over. Be careful out there.
Apr
30
New CAPTCHA Replacement
April 30, 2008 | Leave a Comment
IMAGINATION is a new candidate for replacing CAPTCHA, the recently fallen test for trying to determine if a computer or a person is on the other end of a connection. You’re probably familiar with CAPTCHA as that weird image composed of letters and numbers that you’re asked to read and type in to a box in order to do some operation on the web.
CAPTCHA was cracked some months ago (as I’ve previously mentioned) and one by one, the various implementations have fallen prey to the bots sending you spam.
The IMAGINATION program (click to try it out!) asks you to do two things: recognize images among a tiled set, clicking on the center of any one you choose, and then annotate an image with the correct description from a list of captions.
It will be interesting to see if this stands up to the hackers now that CAPTCHA is all but dead.
[ via Slashdot ]
Apr
30
Ethics prevents acting for good
April 30, 2008 | 2 Comments
Recently, the Kraken botnet has come into focus as the worlds largest, with an estimated number of zombie computers between 165,000 and 600,000. Each of these computers is probably sending you spam right now, and many have probably probed your computer to see if it can be compromised as well. Who knows, maybe your computer is already one of them.
Researchers at TippingPoint started out to determine the size of the network, which they did by building a server of their own, and waiting for zombies to connect to them for instructions. They eventually managed to attract a 25,000 in a week’s worth of time. Here’s where things get interesting.
Most botnets include a feature that lets the controller upgrade the zombie computer with a new version, so the researchers could use their new-found power for good, directing these machines to remove the infection, or render it benign. Due to liability concerns, TippingPoint, the good guys, decided they could not remove the infection.
In a comment attached to Amini’s initial blog post, Endler put it plainly. “Cleansing the systems would probably help 99% of the infected user base,” he said. “It’s just the 1% of corner cases that scares me from a corporate liability standpoint.”
I sympathize with TippingPoint, but it’s a sad commentary on the world when the good guys are afraid of doing something that’s clearly right out of liability concerns. While accessing a computer without the owner’s consent is illegal in the US, shouldn’t a Good Samaritan law apply in cases like this?
[ via CompuWorld ]
Apr
16
The New Covert Channels
April 16, 2008 | Leave a Comment
Back in the days of yore, security professionals used to be interested in things called covert channels. These are ways of communicating information into or out of a secured environment. Admittedly, most people interested in this also dealt with information that had access restrictions on them called things like “Top Secret” and “Special Access Required”. They also had prison sentences attached to disclosing them. Today, there are new covert channels that are far more of a concern. Read more
Mar
26
Paper Enigma
March 26, 2008 | Leave a Comment
During World War II, the Germans widely used several variants of the Enigma machine, which was actually created by a Polish inventor. This same Polish inventor helped the British with their famous project to crack the Enigma, and run by Alan Turing and centered at Bletchley Park.
The basic theory of the Enigma was that you had a number of wheels that had contacts on each side. If you picture a donut, think of sprinkles on both sides and you’ve got the basic idea. Now, if you connect a sprinkle on one side with a sprinkle on the other, but don’t go straight through the donut, you get a degree of obfuscation.
Stack three donuts side by side. The analogy goes a bit awry here, because imagine that we assign each of the sprinkles on each side a letter or number. We pick the letter we want to encode on the left donut, and then run a current through that sprinkle, and you get a current coming out in a pseudo-unpredictable sprinkle on the donut on the right, corresponding to the encoded letter or number. Each time you do encode a character, you rotate the donuts one step. The outer donuts you rotate towards you, and the inner one away. Now run the next current through. That’s how an Enigma works. Here’s an exploded view of an Enigma machine rotor, created by Wapcaplet in Blender.
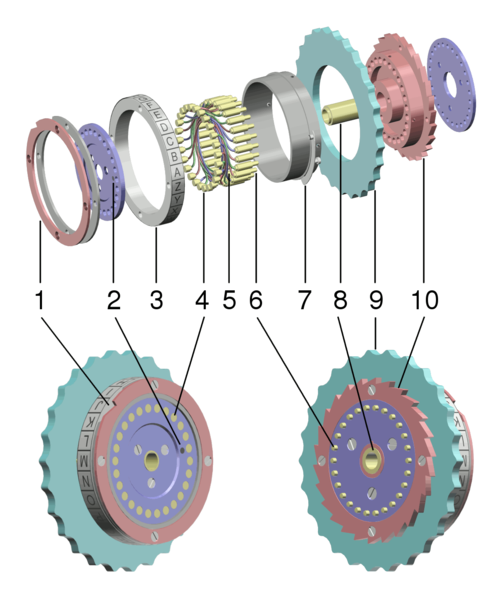
Later versions of the Enigma added a fourth rotor, and some used reflection, which ran the signal back through the rotors once it reached the right hand side.
If you want to try your hand at an Enigma, and don’t want to machine one yourself, Mike Koss has created a nifty paper Enigma for you to try.
« go back — keep looking »Blogroll
- Ars Technica
- Dark Reading - IT Security
- Help Net Security
- InformIT
- SANS Internet Storm Center
- Schneier on Security - Dr. Bruce Schieier’s blog
- Security Info Watch
- What to Fix - Daniel Markham, fellow consultant
- Wired Gadget Lab
- Wordpress Documentation
- WordPress Planet
- Wordpress Support Forum

